Centralized Management and Deployment: A Deep Dive into Group Policy-Based Drive Mapping
Related Articles: Centralized Management and Deployment: A Deep Dive into Group Policy-Based Drive Mapping
Introduction
With great pleasure, we will explore the intriguing topic related to Centralized Management and Deployment: A Deep Dive into Group Policy-Based Drive Mapping. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Centralized Management and Deployment: A Deep Dive into Group Policy-Based Drive Mapping
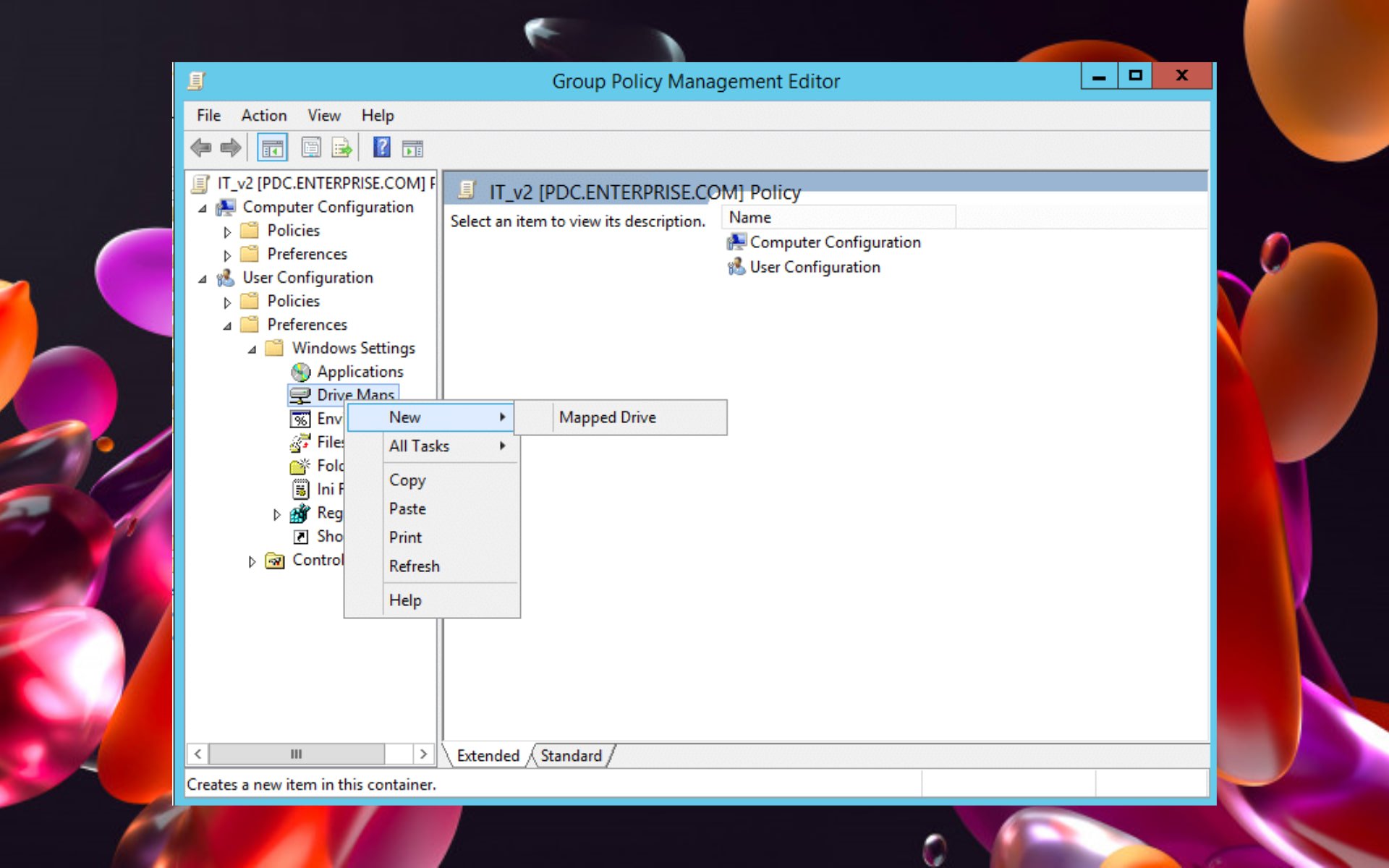
In the realm of network administration, maintaining a consistent and secure environment for user access to shared resources is paramount. This is where Group Policy, a powerful tool within the Windows operating system, steps in, offering a centralized and efficient mechanism to manage various aspects of user and computer configurations. One particularly valuable feature within this framework is the ability to map drives for users, enabling seamless access to shared network locations.
Understanding the Mechanism: A Detailed Look at Group Policy Drive Mapping
Group Policy drive mapping, at its core, leverages a predefined set of rules to automatically connect network drives to user workstations upon login. This process eliminates the need for individual users to manually connect to shared resources, simplifying access and promoting consistency across the network.
How it Works:
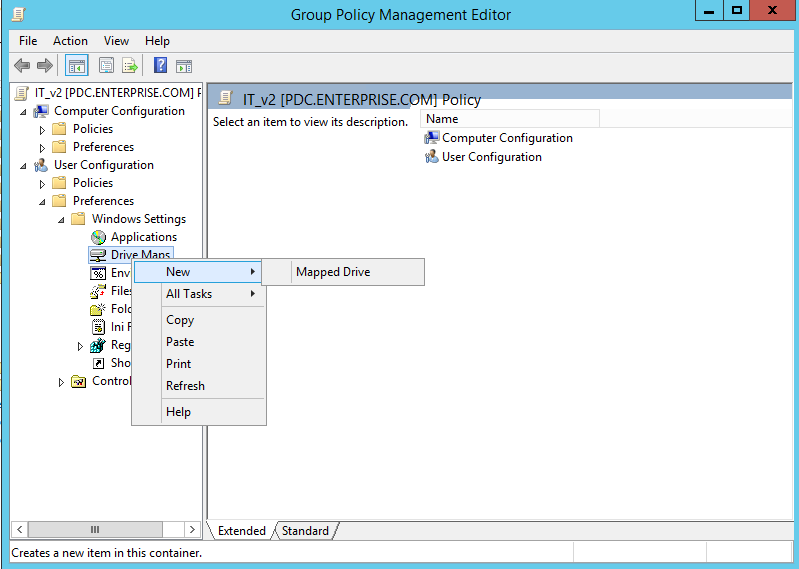
- Policy Creation: Administrators define the desired drive mappings within a Group Policy Object (GPO). This involves specifying the network path of the shared resource, the drive letter to be assigned, and any relevant access permissions.
- Policy Deployment: The created GPO is then linked to specific Organizational Units (OUs) within the Active Directory structure, targeting the desired user groups or computers.
- User Login: Upon logging in, users within the targeted OUs automatically receive the configured drive mappings. The specified drive letters become accessible, allowing users to navigate and access shared resources seamlessly.
Benefits of Group Policy Drive Mapping:
- Centralized Management: This feature empowers administrators to manage drive mappings for a large user base from a single location, streamlining the process and minimizing manual intervention.
- Consistency and Standardization: By applying the same drive mappings across targeted users, administrators ensure a consistent user experience, promoting uniformity and reducing confusion.
- Security Enhancement: Group Policy allows administrators to define access permissions for shared resources, ensuring that users only access the data they are authorized to view. This approach helps safeguard sensitive information and maintain data integrity.
- Simplified User Experience: Users no longer need to manually map drives, eliminating potential errors and simplifying their workflow.
- Improved Resource Management: Administrators can easily monitor and control access to shared resources, ensuring optimal utilization and preventing unauthorized access.
- Enhanced Scalability: As the network grows, Group Policy drive mapping scales seamlessly, accommodating new users and devices without requiring extensive manual configuration.
Beyond the Basics: Advanced Configurations and Considerations
While the fundamental concept of Group Policy drive mapping is relatively straightforward, several advanced configurations and considerations can further enhance its functionality and tailor it to specific organizational needs.
1. Connection Types:
- Persistent Connections: These connections remain active even after the user logs off, ensuring that the mapped drive remains available for subsequent logins.
- Temporary Connections: These connections are only active during the user’s current session. Once the user logs off, the connection is severed.
2. Drive Mapping Options:
- Specific Users: Administrators can target specific user accounts for drive mapping, allowing for tailored access control.
- Specific Computers: Drive mappings can be applied to specific workstations, ensuring that only designated machines have access to particular resources.
- Both Users and Computers: A combination of user and computer targeting allows for granular control over drive mappings, enabling administrators to cater to diverse access requirements.
3. Access Permissions:
- Read-Only: Users can view the contents of the mapped drive but cannot make changes.
- Read/Write: Users can both view and modify the contents of the mapped drive.
- Full Control: Users have complete control over the mapped drive, including the ability to modify permissions and manage files.
4. Drive Letter Assignment:
- Fixed Drive Letters: Administrators can assign specific drive letters to ensure consistency across the network.
- Automatic Drive Letter Assignment: The system can automatically assign available drive letters, providing flexibility for dynamic environments.
5. Scripting and Automation:
- PowerShell: Administrators can leverage PowerShell scripts to automate the creation and management of Group Policy drive mappings, further enhancing efficiency and consistency.
6. Conditional Drive Mapping:
- User Attributes: Drive mappings can be configured based on user attributes, such as department or location, enabling targeted access based on specific user characteristics.
- Computer Attributes: Drive mappings can be applied based on computer attributes, like operating system version or hardware configuration, ensuring tailored access based on the specific device.
7. Security Considerations:
- Authentication and Authorization: Implementing strong authentication measures, such as multi-factor authentication, is crucial for safeguarding access to shared resources.
- Data Encryption: Enabling encryption for shared resources helps protect sensitive data from unauthorized access, even if the network is compromised.
- Regular Auditing: Regularly reviewing access logs and monitoring user activity helps identify and address potential security threats.
FAQs: Addressing Common Concerns
1. How do I troubleshoot drive mapping issues?
Troubleshooting drive mapping issues can involve investigating several factors, including:
- Policy Deployment: Ensure the GPO is correctly linked to the target OUs and that the policy is applied successfully.
- Network Connectivity: Verify that the network path to the shared resource is accessible and that the network connection is stable.
- User Permissions: Confirm that the user has the necessary permissions to access the shared resource.
- Drive Letter Conflicts: Ensure that the assigned drive letter is not already in use by another application or drive.
- Group Policy Processing: Check the Group Policy processing order and ensure that the desired drive mapping policy is being applied correctly.
2. Can I map drives to local folders?
While Group Policy primarily targets network resources, it is possible to map drives to local folders on the user’s machine. This can be useful for redirecting user profiles or specific application data.
3. What are the limitations of Group Policy drive mapping?
- Limited Customization: Group Policy drive mapping offers a high level of control, but there are limitations in terms of highly customized access requirements.
- Network Dependency: The effectiveness of drive mapping relies on a stable network connection. If the network connection is interrupted, mapped drives may become inaccessible.
Tips for Effective Implementation:
- Plan and Design: Carefully plan the drive mapping strategy, considering user needs, security requirements, and network infrastructure.
- Test Thoroughly: Before deploying drive mappings to a large user base, test the configuration thoroughly in a pilot environment.
- Document Processes: Document the drive mapping process and any relevant configurations for future reference and troubleshooting.
- Monitor and Audit: Regularly monitor the drive mapping configuration and user activity to ensure security and optimal performance.
- Stay Updated: Keep abreast of the latest Group Policy features and best practices to enhance your drive mapping strategies.
Conclusion: Optimizing Network Management with Group Policy Drive Mapping
Group Policy drive mapping is a powerful tool for network administrators, enabling centralized management, consistent user experiences, and enhanced security. By leveraging its capabilities effectively, organizations can streamline access to shared resources, optimize network management, and create a more efficient and secure working environment. By understanding the fundamental principles, exploring advanced configurations, and adhering to best practices, administrators can harness the full potential of Group Policy drive mapping to optimize their network infrastructure and empower users with seamless access to critical resources.
Closure
Thus, we hope this article has provided valuable insights into Centralized Management and Deployment: A Deep Dive into Group Policy-Based Drive Mapping. We hope you find this article informative and beneficial. See you in our next article!